Today we are proud to introduce our new Java application security product, Azul Vulnerability Detection. To help explain why it’s so revolutionary compared to other solutions, I’ll use an appropriate analogy for two days after Halloween.
It’s a classic horror movie trope – the hero locks the doors and watches through the windows for the boogeyman, carefully scanning the woods outside the house, only to discover that the assailant is … inside. The bad guy exploited a known vulnerability while the hero was scanning entry points — a broken deadbolt or a loose window — and now there’s a chaotic battle for survival.
Danger lurks where you least expect
In Java, vulnerabilities are unpatched flaws that allow bad actors to get into your application environment where they can do damage. They are most often found in third-party libraries and components that applications use. These helpful components enter customer applications; but if they have unpatched vulnerabilities, they become a growing threat for any organization with a large Java footprint.
For years companies have been incrementally securing all the touchpoints across the software supply chain, flowing left from production penetration testing and environment hardening. But after years of scanning code on its path to production, too often they find the vulnerabilities are… inside the app.
That is, inside production of your live, business-critical Java applications is the final and most valuable touchpoint in the software supply chain. That’s where Azul comes in. Our new security offering, Azul Vulnerability Detection, provides observability of your Java applications to continuously detect known vulnerabilities in production. Azul Vulnerability Detection uses existing information the JVM has from running Java applications to identify vulnerable code that actually runs, eliminating false positives and generating accurate results unattainable by traditional application security tools, with no performance penalty.
The most obvious repercussion of undetected vulnerabilities is the bad guys who will exploit them to compromise company data, steal personally identifiable customer information, and damage your application environments. But the effects of just monitoring and responding are equally insidious.
After years of scanning code on its path to production, too often the vulnerabilities are already inside the app.
Remember in December 2021 when a vulnerability was found in Log4j, a library used very commonly in Java applications? Companies pulled engineers and developers away from their normal jobs to grapple with it, causing missed deadlines and incomplete work. According to a 2022 report by the Department of Homeland Security’s Cyber Safety Review Board, at least one cabinet department spent more than 30,000 hours responding to Log4j.
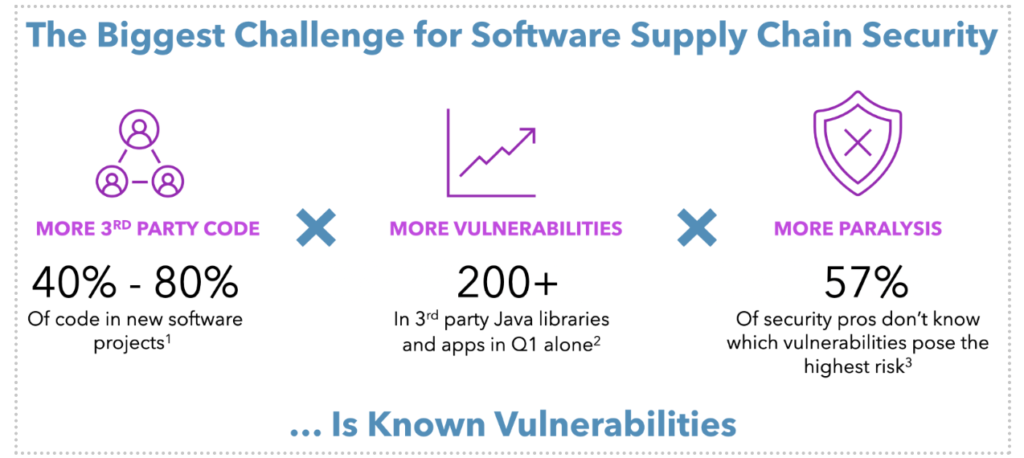
And that’s just one vulnerability. In Q1 2022 alone there were more than 200 known vulnerabilities in third-party Java applications and components, many with the highest risk score. It’s the security version of a zombie apocalypse.
Java application security today: the vulnerability detection landscape
Current tools for detecting common vulnerabilities and exposures (CVEs) operate in different ways. Solutions like Snyk and Synopsys do a terrific job of scanning application source code. They perform static analysis while developers are still writing code to expose errors and vulnerabilities before remediation becomes expensive and messy.
Some tools check access points and simulate attacks, while others like Contrast and Seeker embed agents directly into code.
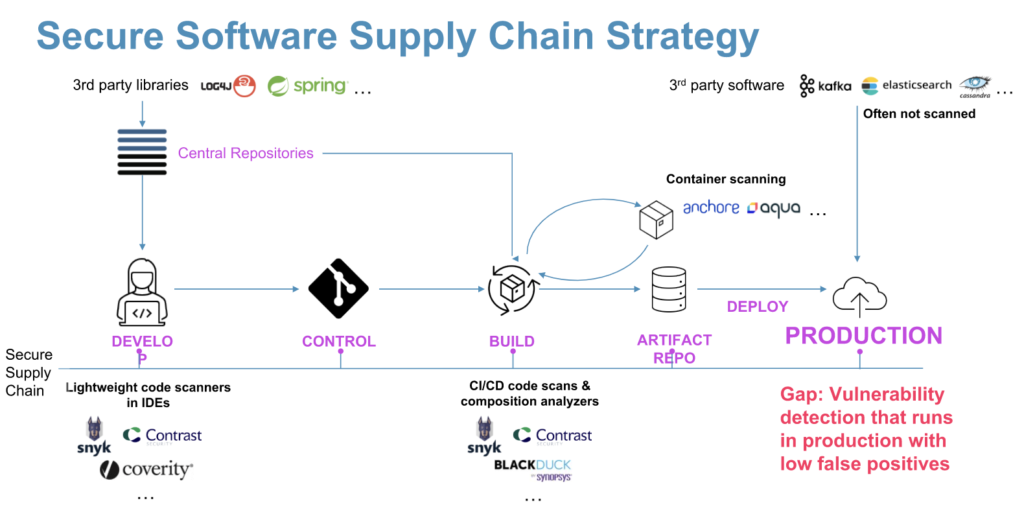
Detecting vulnerabilities requires runtime-level visibility into all Java applications and software, something traditional security tools don’t do. Azul augments existing tools to close the gap.
Azul Vulnerability Detection extends software supply chain security
Azul Vulnerability Detection is a true game changer for Java security. It operates differently than other tools and fills critical gaps in detection. It’s a SaaS solution that delivers a continuous understanding of your Java applications and exposure to known vulnerabilities. For a more complete examination of the product, read Senior Director of Product Management Erik Costlow’s blog post. Let’s look at how Azul Vulnerability Detection provides distinct benefits by working differently from existing tools.
- Delivers greater accuracy: Azul Vulnerability Detection leverages Azul JVMs. It always has a complete inventory of the applications and components running in production, so it doesn’t miss things like traditional scanners can. It compares your environment to a Java-specific CVE database that is updated daily so engineering teams can be instantly aware of a CVE running in production.
- Eliminates false positives: Azul analyzes code executed by Java applications running in production – not just present – so security teams don’t waste time responding to components that don’t represent true danger. This saves your security and engineering teams from unnecessary time away from their core work.
- Allows focused forensics: Azul retains the history of detections so when new CVEs are disclosed, organizations can find out when and on what systems they have been running the vulnerable versions.
- Saves precious person-hours: Since Azul lives in the JVM and sits at the last mile in your software supply chain – production – it sees instantly when a previously patched component has been replaced with a vulnerable one, saving your team from keeping constant eyes on glass.
- Helps relieve the talent gap: Companies are already struggling with a talent gap, and it only gets worse when that talent is getting pulled away from key priorities.
Why now is the right time for vulnerability detection in production
Companies are using more third-party code than ever, which introduces more risk. Gartner estimates that 40-80% of code in new projects is from third parties. Research from IBM says 57% of security professionals don’t know which vulnerabilities pose the highest risk.
Azul is the world’s largest independent provider of OpenJDK and the biggest Java engineering team after Oracle. Security has always been at our core and uniquely qualifies us to lead Java security into new territory:
- Azul is the only company other than Oracle to provide security-only updates
- Azul is a member of the OpenJDK Vulnerability Group
- Azul has been a community leader in Java for more than 20 years
Learn more about Azul Vulnerability Detection
Our security experts and sales folks are ready to talk with you about your secure software supply chain strategy for Java applications. No one approach solves everything, but Azul works with existing solutions to close ranks on vulnerabilities so your engineers and developers can stay safe and focus on their most important work – delivering new products and services to your customers.
Visit Azul Vulnerability Detection on our website for more information and additional resources, including blog posts and white papers to help you become more informed about the product and whether it’s right for you.
We Love to Talk About Java
We’re here to answer any questions about Azul Vulnerability Detection and Java security.