
We have a new resource for Branch Chiefs available for free download called “The Branch Chief’s Guide to Java Security.” This blog explains why you need it and how to get it.
Are you an expert in Java security already? Do you know all you need to know about keeping your agency’s Java estate safe from cyber attacks? If so, good for you! Then you don’t need this blog.
Too Much, Too Often, Too Busy
But of course, technology is technology, and in today’s IT world, everything is related. So if you’re an expert in Java, that must also mean you’re an expert in Python, a fundamental scripting language which, as a Branch Chief, you know is used by Google and NASA, among many others, primarily for experimentation while Java is primarily for production.
As a Branch Chief, you must also be expert in Ruby and Ruby on Rails because this is where much of your web development is done.
And you must also be expert in JavaScript, used for building your agency’s front-end website.
And expert in C, a core language which is best for OSes and AI; and in C++, typically used for search engines and operating systems; and in C# for backend programming; and in PHP for web applications; and in SQL for databases; and in Objective-C for creating Apple apps; and in PowerShell and Bash for coding Windows and Linux-based computing systems.
The list goes on—and that’s just programming languages. Looking at the IT landscape as a whole, the number and variety of technologies you must be an expert in to fulfill your mission, multiplied by their interconnections, and then multiplied again by the velocity of change, is mind-boggling. It’s simply not possible.
Of course, you can’t be an expert in every technology.
Everyone needs a little help from their specialist friends.
Customer Service Is the Mission, but Data Security Is the Law
And what is your mission exactly? According to an Executive Order from President Biden, the current policy priority is “transforming federal customer experience and service delivery to rebuild trust in government.”
Technology is key to your ability to support the mission of transforming customer experience. At the same time, you must ensure the security of all this technology—that’s the law.
The Federal Information Security Management Act (FISMA) makes agency heads responsible for maintaining protections commensurate with the risk of harm of a compromise. In practice, this responsibility falls on your shoulders—i.e., the Branch Chiefs who are responsible for mission-enabling IT.
You’re Constantly Under Cyberattack
The responsibility on your shoulders is magnified because we are in a state of attack on the IT front.
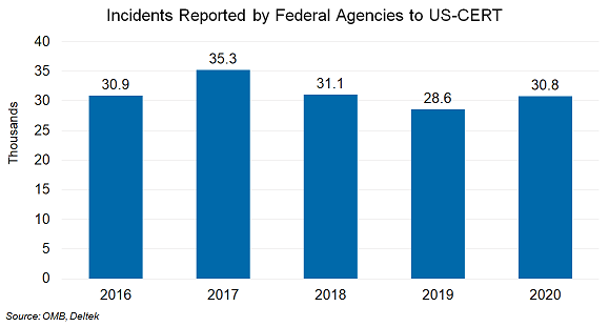
Cyber attackers launched nearly 31,000 attacks in 2020 against federal agencies, an average of 84 a day, as shown to the left[1]. Hackers are trying to sniff out vulnerabilities in every corner of your IT estate 24×7.
And last December they found a big one: the Log4j vulnerability.
Log4j Is One of the Worst Security Vulnerabilities Ever
What makes the Log4j vulnerability so dangerous is that 1) Java is everywhere; 2) Log4j, while not part of the Java code, is a simple-to-use, open-source logging library that’s been deployed in possibly billions of devices, enterprise applications, and cloud services; 3) the Log4j code is buried in layers of code and not always easy to find (in order to remediate the issue); and 4) Log4j is very easy to exploit remotely just by entering a single line of code.

“The log4j vulnerability is the most serious vulnerability I have seen in my decades-long career.”
- Jen Easterly, security director, U.S. Cybersecurity and Infrastructure Security Agency [2]
You Need Expert Help to Master This Challenge
Again, if you’re a Java expert and confident in your encyclopedic knowledge, go forward and defeat Log4j with our blessing.
But, if you’re like most Branch Chiefs, you could use a little help from your expert friends as you face the bewildering array of technologies for which you are responsible.
The U.S. Transportation Command Trusts Azul for Secure Java
The United States Transportation Command (USTRANSCOM) needed a little help from the Java experts in 2020 when they decided to replace Oracle Java SE with Azul Zulu builds of OpenJDK.
USTRANSCOM chose Azul over other OpenJDK commercial offerings based on Azul’s substantially lower Java support costs, superior security offerings, and better service SLAs and support response times.
USTRANSCOM is a unified, functional combatant command which provides support to the other ten U.S. combatant commands, the military services, defense agencies, and other government organizations. Composed of three service component commands—the Air Force’s Air Mobility Command, the Navy’s Military Sealift Command, and the Army’s Surface Deployment and Distribution Command—USTRANSCOM coordinates missions worldwide using both military and commercial transportation resources.
Clearly, Azul has an extensive footprint and deep expertise in Java as used in highly sensitive government applications. In addition to USTRANSCOM, Azul public-sector customers include the Department of the Interior, the Federal Reserve System, and US Courts.
A Free Guide to Java Security
The Java experts at Azul have created a free guide to help you with Java security, with a focus on the Log4j vulnerability.
Download “The Branch Chief’s Guide to Java Security” here.
This guide provides best practices from the Java experts as a starting point for not only defeating Log4j and other adversaries in the cyber war, but also for improving the overall security of your Java estate.
Sources
- https://iq.govwin.com/neo/marketAnalysis/view/OMB-Cybersecurity-Metrics-Show-Agencies-Struggle-to-Report-Effectively/5951?researchTypeId=1
- https://www.washingtonpost.com/technology/2021/12/20/log4j-hack-vulnerability-java/




